Tetration is Cisco’s holistic workload protection for multi-cloud data centers. The implementation of a zero-trust model allows users to identify security incidents faster, contain lateral movement and minimize their attack surface. Its infrastructure-agnostic approach supports both on-premises and public cloud workloads.
How does it work?
Tetration is one of the most powerful data center telemetries and analytics platform in the industry, being the only platform that can capture every packet and every flow at line rate It applies machine learning and intelligent algorithms to analyze every packet in real time and deliver actionable visual insights inside the working of an infrastructure.
Moreover, it has software sensors built into the Cisco Nexus 9000 CloudScale switches provide added telemetry vantage points for an even more granular analysis. These software sensors also act as enforcement points for segmentation and collect the following telemetry data:
- Flow Information
- Interpacket variation
- Process details
- Software packages
Major Features
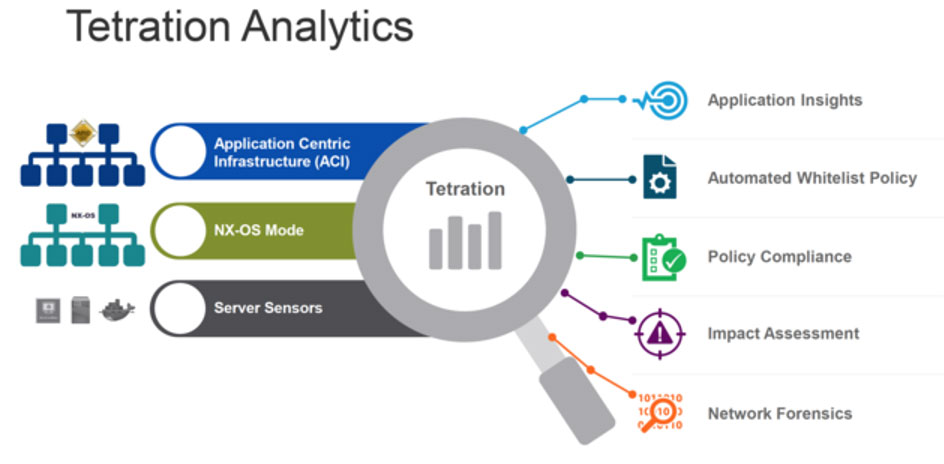 Automated Whitelist Policy Generation
Automated Whitelist Policy Generation
The Tetration platform can be used to automatically generate particular whitelist policies based on application-communication behavior and dependency although automatic generation is not a limitation to a user’s wish to add more policies. The user can add other predefined policies from higher level entities such as security operations. Policies can also be specified using tags and annotations.
Scalable Policy Enforcement
Application segmentation in Tetration allows network administrators to use an auto-generated application-whitelist policy to implement a secure, zero-trust model. Before enforcing the policy, it is normalized based on the priority and hierarchy. This type of approach delivers a stateful and consistent segmentation across multi-cloud data centers at scale.
Process Behavior Baseline and Deviation
A data center telemetry and analytics platform like Tetration collects and baselines the process details running on each on the servers. Based on this data and the presence of algorithms to understand them, Tetration can track behaviors pattern changes and match those to malware behavior patterns. Security events are raised for such deviations for the alert of the user.
Software Vulnerability Detection
The Tetration platform features a 19 years’ worth of Common Vulnerability and Exposures (CVE) database. Information like installed software packages, package version, patch level, etc. is used by Tetration to identify vulnerabilities stored in the CVE database. Thus, all the affected servers can be quickly identified and quarantined with Tetration.
Tetration is just one of the many tools that BayInfotech employs in its IT management services to help our clients reap the maximum benefits from the least amount of resources. Contact us today for a demo worth your time and your business’ future.